The years 2020 and 2021 were characterized by a mass scale transition towards remote work. This not only opened up new vulnerabilities for cyber criminals, but also increased the overall threat surface of enterprises.
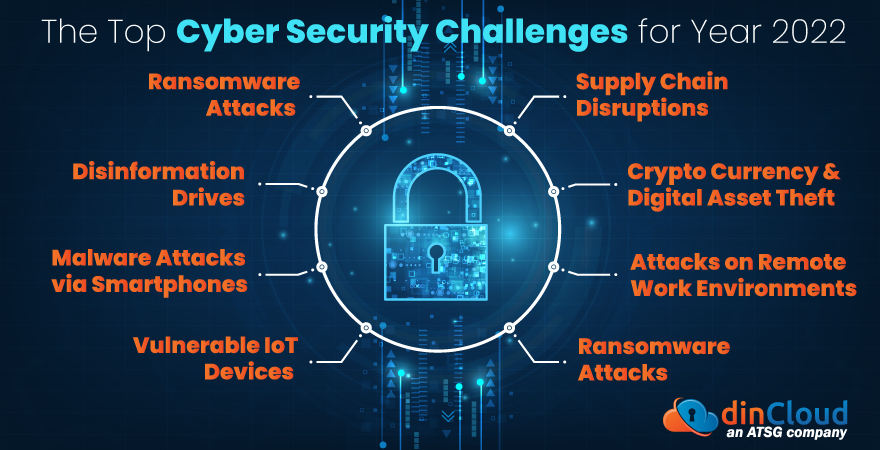
In this post, we will briefly list down some of the top cyber security challenges for business globally. In a nutshell, enterprises need to adopt a proactive approach towards the present day cyber security challenges.
Related: How to Develop a Holistic Approach Towards Cloud Security?
Ransomware Attacks
These have been some of the most “lucrative” forms of cyber attacks out there. Attackers in this case tend to exploit the slightest vulnerability within remote work solutions, and plant the malware within enterprise networks.
This malware then encrypts all the enterprise data, locking it out for the compromised business. In exchange for decrypting your very own data, your enterprise will be forced to pay a hefty ransom, which is otherwise prohibited by law in most jurisdictions.
Related: How to Navigate Cloud Security Challenges in the Year 2022?
Supply Chain Disruptions
In the present time, cyber criminals are also becoming ever more crafty. What they have realized is that by compromising global supply chain systems and operations, they can cause mass scale disruptions that impact millions of people across the globe.
Disinformation Drives
Cyber criminals these days are exploiting the power and outreach of social media platforms for spreading disinformation about certain companies or events. This not only hurts the reputation of the entity concerned, but also propagates undue panic among the masses.
Related: Cloud Security Trends to Look Out For in Year 2022
Crypto Currency and Digital Asset Theft
Digital wallets that hold the tangible wealth of masses in the form of crypto currencies are always under the radar of cyber miscreants. They constantly scour these platforms housing digital assets for any vulnerabilities, and depriving people from their wealth.
What makes this area very lucrative for cyber criminals is the loose regulatory framework around crypto currencies, and similar digital assets. There are also glaring question marks on whether digital assets like crypto currencies will ever be fully legitimized by regulators.
Malware Attacks via Smartphones
In the present day and age, the role of smartphones in our daily lives is touching unprecedented levels. Most of our day to day tasks like banking, shopping and travelling etc. are now being managed via ultra powerful smartphones.
Related: Security Benefits of Cloud Computing Solutions
However, cyber miscreants are using shady smartphone applications and other impersonation techniques to plant malware. This in turn triggers a chain reaction that can include information theft, unintended financial transactions and other risks.
Attacks on Remote Work Environments
Many businesses have resorted to remote work in response to the pandemic. However, instead of using secure remote work platforms like Cloud Computing, some businesses are still using legacy systems to support loosely secured remote work environments.
The vulnerabilities inherently present in un-structured remote work tools act as a point of entry for cyber miscreants to gain access to enterprise networks. Once this happens, the compromised organization can fall prey to many forms of cyber attacks within no time.
Vulnerable IoT Devices
While Internet of Things (IoT) is the next big item in our lives, the security of IoT devices has a lot of catching up to do. Loosely secured IoT devices pose serious vulnerabilities for entire IoT and edge networks, and the security of such devices is very essential.
As the digital footprint of both enterprises and individuals grows with every passing day, so does the accompanying threat surface. Given the nature of present day cyber threats, and their disruptive impact, the best and only recourse is preventive measures.
The sheer cost, time and risks of recovering from a cyber attack can be too overwhelming for even a well established organization. Enterprise systems and mechanisms will have to stay one step ahead of the above cyber threats to stay safe.
Lastly, investing time and resources in making your workforce more aware of the telltale signs of cyber threats also goes a long way in improving your preventive posture. A proactive approach towards cyber security is your best bet against most threats.
Contact dinCloud for a wide array of cloud computing solutions and services that come with multi layered security built into the very service.


