A Managed IT Partner That Thinks Like You — And Gets IT Done
We don't replace your team - we amplify it. From security to cloud optimization and network performance to collaboration, we provide the expertise, framework and support you need to keep your operations running. No fluff. No finger-pointing. Just IT that works.
Secure. Scalable. AI-Powered. | Integrated with your tech stack. | Built-on industry leading platforms.
Trusted By Mid-Size and Enterprise-Size Customers


























From IT Chaos to IT That Works
Our Comprehensive IT Platform Optimizes Your Tech Stack and Keeps Your Critical Applications Always-On and Secure
Today's IT Reality: What You Are Up Against
Rising threats. Expanding complexity. Stretched teams. IT is expected to do more with less—again. You need a partner who understands the impossible expectations you face daily and can help you modernize, secure, and streamline operations without adding to the noise.
Complexity
Disjointed platforms, cloud sprawl, and hybrid work environments create inefficiencies that slow your team down.
Security
Resources
XTIUM:
Your IT Force Multiplier
We're not just another MSP—we're your strategic ally. No band-aid fixes. No endless ticket queues. We take ownership of your IT challenges, solve problems with urgency and deliver solutions that transform your IT from a cost center to a competitive advantage.
- Full-stack support tailored to your needs
- Hands-on, high-touch service—no excuses
- Deep technical expertise that integrates with your team
A Complete Suite of AI-Powered, Secure, Scalable IT Solutions
Built on Industry-Leading Platforms. Delivered By One Trusted Partner.
Virtual Desktops
Managed Security
Managed Network
Unified Communications
IT
Helpdesk
AI
Consulting
 Virtual Desktops
Virtual Desktops
Fast, secure access to company apps & data on any type of end-point device.
- Flexible, multi-cloud, multi-vendor deployments for secure remote and hybrid work
- Reduce maintenance headaches with centralized management
- Ensure compliance with built-in security controls
Managed Security
AI-driven detection and 24x7 SOC monitoring to prevent, mitigate, and recover from modern threats—fast
- AI-driven threat intelligence to detect real threats and eliminate false positives
- Actionable, data-driven insights to proactively mitigate threats before impact
- Continuous security management with real time incident response
Managed Network
Gain full visibility into your network with trusted observability, real-time analytics, and reliability
- 24/7 full stack monitoring and detection to ensure a secure and reliable network
- First touch resolution and automations to resolve issues before they impact operations
- Customized runbooks, change management and onboarding support to enhance efficiency
Unified Communications
Communication and collaboration tools that unify your systems instead of creating more silos
- Natively integrated with Microsoft Teams and Cisco Webex to deliver a frictionless user experience
- Proprietary omnichannel contact center that delivers a unified agent and customer experience
- Advanced features such as compliant call recording, reporting and open API integrations
IT Helpdesk
24x7 support from experts who solve problems, fast—not just log tickets.
- 24/7 responsive support for all IT issues
- Rapid resolution of technical problems
- Knowledgeable technicians who understand your business
AI Consulting
Hands-on advisory service that helps IT leaders build AI strategies that actually work
- Structured assessment to help your organization evaluate, plan, and implement AI the right way
- Comprehensive approach that addresses people, processes, and governance,
- Monitor, refine, and improve AI performance with real-world feedback and ongoing adjustments
- Secure, cloud-based desktops for seamless remote and hybrid work
- Reduce IT overhead with centralized management
- Ensure compliance with built-in security controls
- AI-driven threat intelligence to detect and neutralize cyber risks
- Proactive security operations that mitigate threats before impact
- Continuous monitoring to safeguard sensitive data and systems
- Ensure high-speed, secure, and reliable network performance
- Reduce outages with proactive monitoring and support
- Optimize bandwidth for business-critical applications
- Cloud-based voice, video, and messaging for modern workplaces
- Secure and seamless communication across teams and locations
- Enhanced customer engagement and internal productivity
- 24/7 responsive support for all IT issues
- Rapid resolution of technical problems
- Knowledgeable technicians who understand your business
- IT strategy consulting to align technology with business goals
- Digital transformation support for modernizing IT
- Customized solutions for unique operational challenges
Industry-Recognized, Award-Winning Solutions

3x Leader, Gartner Magic Quadrant for Managed Network Services
Discover why XTIUM (formerly ATSG) has been named a leader in Gartner® 2024 Magic Quadrant™ for Managed Network Services for 3 consecutive years.

2x Challenger, Gartner Magic Quadrant for Desktop as a Service
Last year, Gartner® has released its second ever Magic Quadrant™ for Desktop as a Service (DaaS) report, evaluating DaaS providers on the basis of their Completeness of Vision and Ability to Execute.
The XTIUM Difference: IT That Works Without Headaches
One Partner, Total Accountability
AI-powered, Proactive Security
Predictable Costs, Scalable Support
Reduced Complexity, Optimized IT
Scalable, Future-Ready IT
Deep Expertise, Real Results
Find your solution:
Don't Take Our Word For It. See What Our Clients Have To Say.
Larry H.

Ryan Easter

Jeff Francis

Dan Sincavage

Ken Schultz

Chief Information Officer, Friedman, LLP

Charles Halfpenny
Larry H.

Ryan Easter

Jeff Francis

Dan Sincavage

Ken Schultz

Chief Information Officer, Friedman, LLP

Charles Halfpenny
Larry H.
Now Is The Time to Rethink IT.
Work with a partner that is your IT force multiplier. A partner that makes IT work - just like you would if you had time and resources.

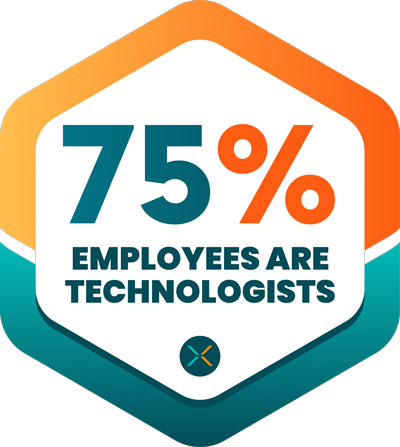
Industry-recognized and certified to support your IT needs
Trusted by 1,400+ mid-size and enterprise companies, we operate as an extension of your team—solving problems with urgency and accountability so you can focus on strategy, not firefighting. Our deep bench of technology specialists brings proven frameworks and real-world experience to help you secure, scale and streamline operations with fewer resources. Stop juggling vendors. Stop fighting uphill battles. Work with an IT partner who gets IT.